Using Groups with Single Sign-On
If your institution uses a CAS or SAML server for single sign-on (SSO), you will need to make sure that each user who will log in through SSO is a member of at least one group within MAPS. This can be either a MAPS group, or an LDAP group that is defined within MAPS.
- When you add LDAP groups in MAPS there is a field which associates the name of the group with the DN or Distinguished Name. For LDAP groups, the DN in the server response is compared to the entry in the Distinguished Name field. The name of the group in MAPS doesn't need to match.
- When you are using MAPS groups, the name of the group in MAPS needs to match exactly with the name that's coming back from CAS or SAML server response.
Note: If the Synchronize SAML users with local MAPS users check box is checked on the Edit Single Sign-On Server dialog, then users will not be required to be a part of a group in order to authenticate. Users will still need to be added individually in MAPS if they are not a member of a group in order to match the SAML NameID with the user name in MAPS. Most of the information of this page is relevant to users who leave the check box unchecked.
Before you set up your groups in MAPS, you must know how the group names are formatted in the response returned from the SSO Identity Provider (IdP). Refer to the documentation for your IdP, or consult the administrator if you are not sure.
DN (Distinguished Name) Response Format
A Distinguished Name response typically looks like this for a SAML SSO server:
<saml2:AttributeStatement>
<saml2:Attribute FriendlyName="memberOf" Name="memberOf" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:uri">
<saml2:AttributeValue>CN=Report Writer,OU=Groups,DC=Evisions,DC=com</saml2:AttributeValue>
<saml2:AttributeValue>CN=Report Viewer,OU=Groups,DC=Evisions,DC=com</saml2:AttributeValue
</saml2:Attribute>
</saml2:AttributeStatement>
A similar response format for a CAS SSO server might look like this:
<cas:serviceResponse xmlns:cas='http://www.evisions.com/cas'>
<cas:authenticationSuccess>
<cas:user>P1234567</cas:user>
<cas:attributes> <cas:CN>P1234567</cas:CN> <cas:Groups>CN=Report Writer,OU=Groups,DC=evisions,DC=com</cas:Groups> <cas:Groups>CN=Report Viewer,OU=Groups,DC=evisions,DC=com</cas:Groups> </cas:attributes>
</cas:authenticationSuccess>
</cas:serviceResponse>
Responses in this format typically come from an LDAP server, and can be used to identify a user's group membership in either the LDAP system or within MAPS.
The following sections explain how to set up groups within MAPS Config to recognize responses in this format so that an authenticated user is matched to the correct group or groups within MAPS
Using a DN Response with LDAP Groups
Using MAPS Config, you would configure the Report Writer group to use the DN from the SSO server like this:
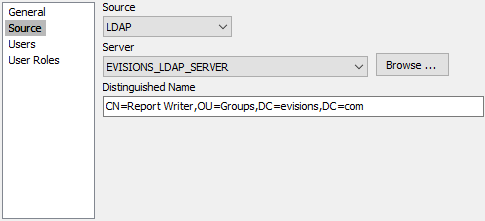
When a user enters valid credentials to the SSO server, the SSO server responds with information about the user. When MAPS receives the response from the SSO server that includes the CN=Report Writer,OU=Groups,DC=evisions,DC=com attribute, MAPS identifies the user as a member of the Report Writer group.
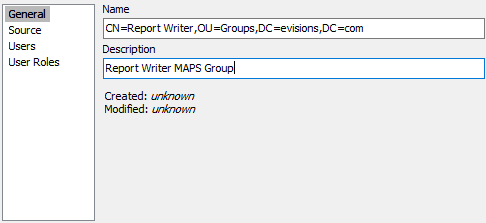
Using a DN Response with MAPS Groups
If you cannot configure LDAP groups within MAPS, you can still use a DN response to identify a user as a member of a MAPS group. To do this, you must name the MAPS group to match the DN attribute exactly.
For example, using the above example, you would configure a group like this:
Other Response Formats
The response from your SSO authentication server might not identify group membership using the DN format. An attribute statement that does not include DNs might look similar to this for a SAML server:
<saml2:AttributeStatement>
<saml2:Attribute FriendlyName="memberOf" Name="memberOf" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:unspecified">
<saml2:AttributeValue>Report Writer</saml2:AttributeValue>
<saml2:AttributeValue>Report Viewer</saml2:AttributeValue>
</saml2:Attribute>
</saml2:AttributeStatement>
In this case, you use MAPS Config to add a group with a name that matches the attribute value exactly. For this example, the name is "Report Writer":
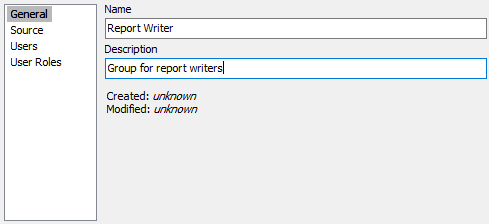
Note that the Source for this group is selected as MAPS: